Solana Under Fire Following “Private” Network Update
Are private network updates that protect Solana a threat to decentralization?
- Published:
- Edited:
A recently published Solana Foundation post-mortem has attracted ire and derision from Solana’s critics, questioning whether the network is truly decentralized.
Facing renewed centralization FUD, Solana thought leaders have deflected criticisms back to rival networks and asserted these issues affect Proof-of-Stake networks across the industry.
Should large validators be able to “privately collude” and make time-sensitive network updates to protect user funds? Or is this fundamentally anti-crypto behavior?
Solana Foundation Releases Post-Mortem
On May 2nd, 2025, the Solana Foundation published a post-mortem detailing the network’s response to a security vulnerability in the ZK El Gamel Proof program. The vulnerability, which allowed for arbitrary proofs to be created that the program would deem as ‘valid’, was originally reported on April 16.
Engineers from reputable Solana teams, including Anza, Firedancer, and Jito, alongside third-party security firms OtterSec, Neodyme, and Asymmetric Research, crafted a timely patch to resolve the vulnerability.
On April 17, Jito and the Solana Foundation privately contacted certain validator operators and informed them of the patch, effectively ensuring that a supermajority could implement the update before any malicious actors took advantage of the vulnerability and exploited the ZK El Gamel program. A second patch addressing a similar issue elsewhere was later audited by security firms and shared with validators.
After a supermajority of network stake had adopted the patch, the Solana Foundation publicly announced the update on April 18. At press time, there has been no loss of funds or known exploit of the ZK El Gamel Proof vulnerability.
Detractors Attack Solana Decentralization
While ecosystem engineers’ and validators’ timely action may have saved user funds, the incident has reignited criticism of Solana's decentralization.
Detractors argue that several key operators privately coordinating to implement a network update is against the ethos of decentralization. Some critics even suggested that the same operators could also collude maliciously to steal user funds.
Solana thought leaders have hit back at these claims, highlighting that it is common for validators to privately resolve and address vulnerabilities before broadcasting them to the public. Revealing the vulnerability and opening up its handling to public discourse is far more likely to result in an exploit if the issue is known to all network participants.
Contrary to criticism from supposed decentralization purists, pre-announcing vulnerabilities before finding solutions is historically a bad idea. In 2021, an Ethereum validator client, Geth, publicly shared a vulnerability before implementing a patch, resulting in an exploit and a minority fork of the chain. In a post-mortem, gETH reportedly acknowledged that this was a “dangerous decision” that it would be “unlikely” to repeat.
Additionally, Solana Labs co-founder Anatoly Yakovenko highlighted that Ethereum, and the wider pool of Proof-of-Stake networks, bear a similar risk profile.
Network stake across leading protocols is typically concentrated among exchanges and professional validator operation firms. Despite Ethereum’s higher validator count, Yakovenko argues that the same operators that dominate Solana stake carry similar influence on Ethereum and other PoS chains.
Reinforcing the arguments supporting Solana decentralization, experts reminded detractors of the network’s recent rejection of SIMD-0228. Overruling influential Solana figures like Yakovenko, Mert Mumtaz, and Multicoin Capital, Solana validators voted resoundingly against a proposal that would’ve priced out smaller operators and concentrated network stake into an elite group of larger validators.
Validator Questions Patch Handling
Though the initial patch distribution may have been private, some validators have suggested that operators should find more obscure ways of communicating when it's been implemented.
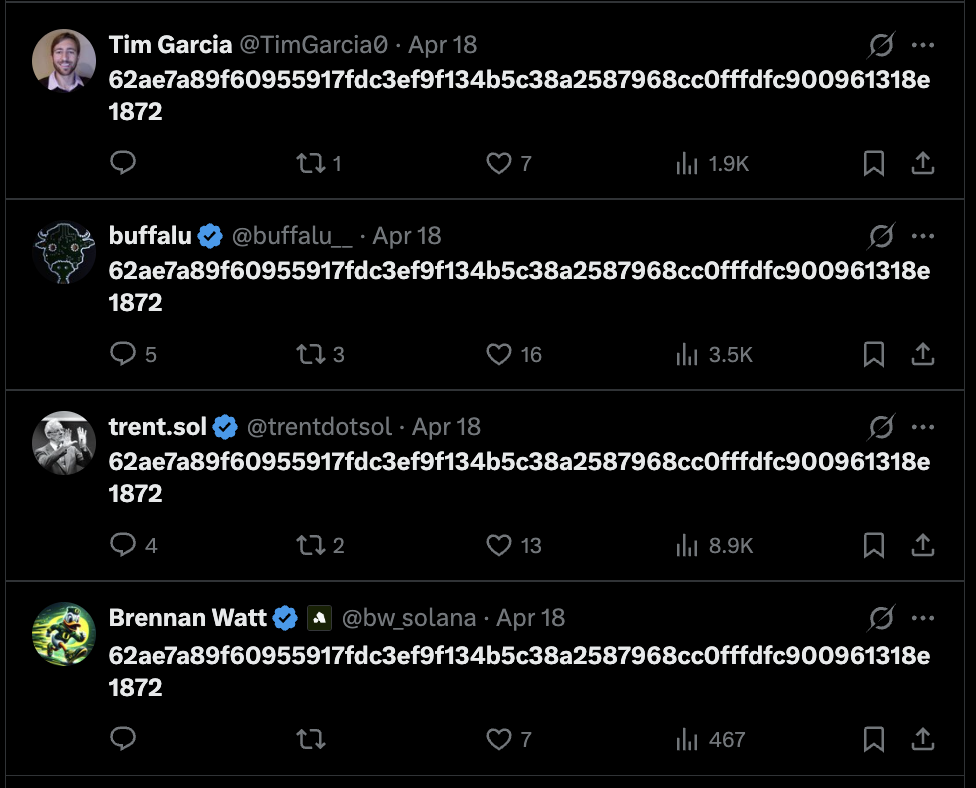
On April 16, before the vulnerability and patch went public, dozens of operators began posting a hash on 𝕏, likely as a means of verifying a message related to a critical patch.
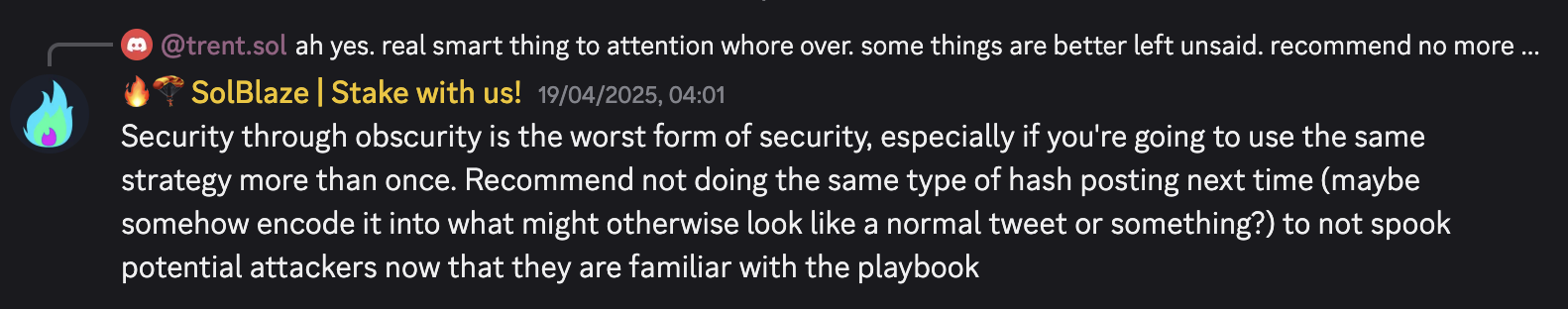
SolBlaze, a long-standing Solana validator, has argued that these verifications should be broadcast in a more obscure way. If a hacker were aware of the vulnerability, but waiting for the opportune moment to exploit the program, seeing critical patch hashes across social media could prompt them to launch an attack before the vulnerability was resolved.
Read More on SolanaFloor
Solana DePIN wades further into legacy telco market
AT&T Embraces Helium DePIN to Boost Coverage and Enhance Services Across America
What Are Solana Validators