Confronto tra le tecnologie DeCC - MPC è l'approccio più equilibrato per la privacy e le prestazioni della blockchain?
Le tecnologie di Confidential Computing decentralizzate come MPC e ZK mirano a rendere le blockchain più sicure su scala, ma come funzionano esattamente?
- Pubblicato:
- Modificato:
Termini come ZK-Proofs, Fully Homomorphic Encryption (FHE) e Multi-Party Computation (MPC) sono spesso utilizzati nello spazio crittografico. Eppure, molti appassionati di crittografia si stanno ancora grattando la testa chiedendosi come queste tecnologie possano effettivamente migliorare le reti blockchain e le applicazioni che supportano.
Grazie all'infinita diffusione dei Layer-2 ZK-rollup nel panorama di Ethereum, lo ZK-proofing è probabilmente la tecnologia DeCC (Decentralized Confidential Computing) più conosciuta nel settore delle criptovalute. Tuttavia, questo non significa necessariamente che sia la più efficace.
Quali sono i pro e i contro dei vari approcci DeCC e come si adattano ai diversi risultati?
Tecnologie DeCC: Un confronto
Quando si parla di informatica confidenziale, non esiste un approccio univoco che vada bene per tutti. Analogamente al famoso Trilemma della Blockchain di Vitalik Buterin’le tecnologie DeCC spesso superano le prestazioni in un'area a scapito di un'altra.
Ad esempio, i Trusted Execution Environments (TEE) sono soluzioni basate sull'hardware che sono probabilmente più sicure e scalabili di quelle basate sul software.
Tuttavia, questa è un'arma a doppio taglio. I TEE non hanno la flessibilità delle tecnologie DeCC basate su software e si affidano a fornitori e produttori di hardware.

Quali sono le tecnologie di miglioramento della privacy più adatte alle esigenze informatiche generali di riservatezza?
Computazione multiparte (MPC)
La MPC è una tecnica crittografica che consente a più parti di calcolare una funzione mantenendo tali input privati e riservati. Consente ai partecipanti di collaborare ai calcoli senza rivelare i propri dati individuali agli altri e a terzi in agguato.
MPC garantisce sia la privacy che l'accuratezza, anche se alcuni collaboratori cercano di deviare dal protocollo. Questo approccio DeCC è particolarmente utile in scenari in cui più entità devono eseguire calcoli e accedere a dati sensibili, come nei servizi finanziari o nei sistemi di voto sicuri.
Pro
- .
Maggiore sicurezza grazie a una gestione distribuita delle chiavi
. -
Elimina i singoli punti di guasto
-
Mantiene la privacy dei singoli ingressi
-
Flessibile per varie applicazioni
Cons
-
Può essere intensivo dal punto di vista computazionale
. -
Può introdurre latenza nelle transazioni
-
Richiede la coordinazione tra più parti
Ambienti di esecuzione affidabili (TEE)
I TEE sono aree sicure all'interno di un processore che garantiscono la riservatezza e l'integrità del codice e dei dati contenuti al loro interno. Forniscono un ambiente di esecuzione isolato basato sull'hardware che protegge le operazioni sensibili da fattori esterni, come il sistema operativo del computer.
In teoria, i TEE offrono un livello di sicurezza più elevato rispetto alle soluzioni solo software, sfruttando le caratteristiche hardware per creare un'area fidata per l'elaborazione di informazioni sensibili.
Gli ambienti di esecuzione affidabili sono spesso utilizzati nei dispositivi mobili, nel cloud computing e in altri scenari in cui gli sviluppatori richiedono un'elaborazione sicura dei dati su scala.
Pro
-
Sicurezza a livello hardware
-
Più veloce delle soluzioni basate su puro software
-
Può gestire operazioni sensibili in un ambiente isolato
Cons
-
Affidamento ai produttori di hardware
-
Potenziali vulnerabilità nell'implementazione dell'hardware
-
Flessibilità limitata rispetto alle soluzioni software
Prove a conoscenza zero (ZK)
Una delle parole d'ordine preferite della crittografia, le Zero-Knowledge Proofs consentono a una parte (il prover) di dimostrare a un'altra parte (il verificatore) che un'affermazione è vera senza rivelare alcuna informazione sul contenuto dell'affermazione stessa.
Le prove ZK forniscono forti garanzie di privacy pur consentendo la verifica di specifiche affermazioni o calcoli. Le prove a conoscenza zero offrono un potente strumento per mantenere la privacy durante le interazioni onchain.
Tuttavia, la tecnologia ZK-proof spesso si basa su un ‘trusted setup’, che richiede alle parti di fidarsi l'una dell'altra fino a un certo punto prima di generare le chiavi che mantengono il sistema di prova. In un certo senso, questo elimina l'efficacia della crittografia a prova di zk.
Pro
-
Fornisce forti garanzie di privacy
-
Riduce la quantità di dati necessari per la verifica
Cons
-
Può essere computazionalmente costoso
-
Può richiedere ‘configurazione fidata’ in alcune implementazioni
.
Crittografia completamente omomorfa (FHE)
Infine, la crittografia completamente omomorfa consente di eseguire calcoli su dati crittografati senza decifrarli. Con FHE, i dati possono rimanere criptati durante l'intero processo di calcolo e anche i risultati rimangono criptati.
Questa tecnologia consente l'outsourcing sicuro di calcoli su dati sensibili, rendendola particolarmente preziosa per il cloud computing e gli scenari di analisi dei dati. Se da un lato FHE offre alti livelli di privacy dei dati, dall'altro deve affrontare notevoli problemi di prestazioni che ne limitano la scalabilità.
Pro
-
Consente di effettuare calcoli sicuri su dati sensibili
. -
Mantiene la privacy dei dati durante l'intero processo di calcolo
. -
Utile nel cloud computing e nell'analisi dei dati
Cons
-
Estremamente intensivo dal punto di vista computazionale
-
Bassa scalabilità
In sintesi
|
Tecnica |
Privacy |
Performance |
Flessibilità |
|
MPC |
Alto |
Moderato |
Alto |
|
TEE |
Moderato |
Alto |
Basso |
|
ZK |
Alto |
Basso |
Alto |
|
FHE |
Molto Alto |
Basso |
Alto |
In sostanza, la questione si riduce a questo: Le diverse tecnologie DeCC sono più adatte a diverse applicazioni. FHE potrebbe essere una delle tecnologie di calcolo confidenziale più private e sicure disponibili, ma soffre ancora di problemi di bassa latenza e di scalabilità.
Invece, i TEE sono alcuni degli ambienti più performanti per l'elaborazione dei calcoli, ma la loro dipendenza dall'hardware significa che possono mancare della flessibilità necessaria in un settore in rapida evoluzione.
Tutto sommato, la Computazione Multi-Party offre forse l'approccio più equilibrato all'elaborazione decentralizzata riservata. Distribuendo il calcolo su più input, l'MPC elimina i punti singolari di fallimento, pur garantendo livelli sufficienti di prestazioni.
MPC in azione: Arcium

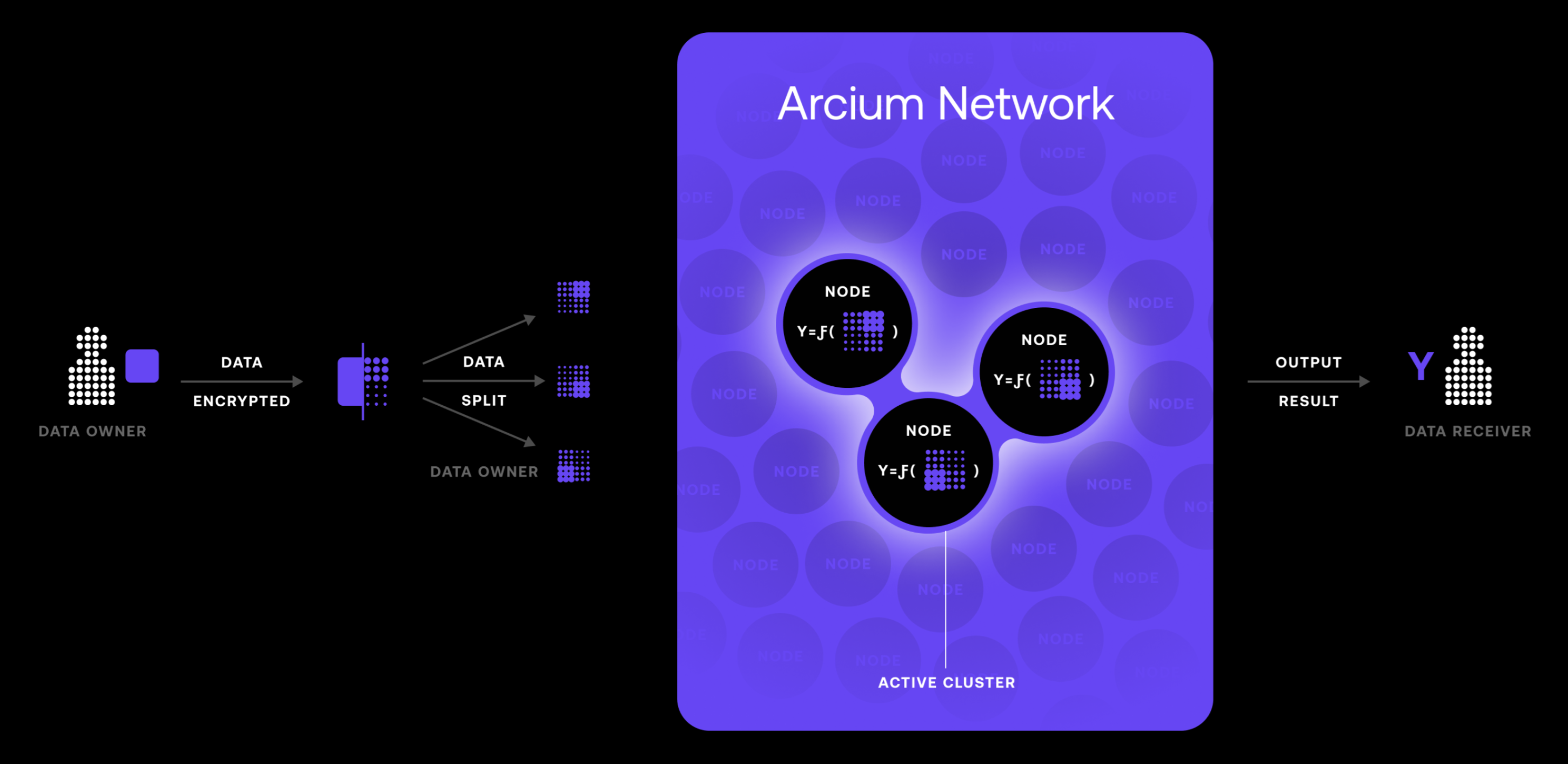
Arcium, un protocollo DeCC basato su Solana, sfrutta MPC per alimentare la sua rete computazionale sicura e performante.
La rete di Arcium è costituita da più nodi chiamati Arx, che elaborano collettivamente dati criptati utilizzando i protocolli MPC. Questa architettura distribuita assicura che nessun singolo nodo abbia accesso all'intero set di dati, migliorando la sicurezza ed eliminando i singoli punti di guasto.
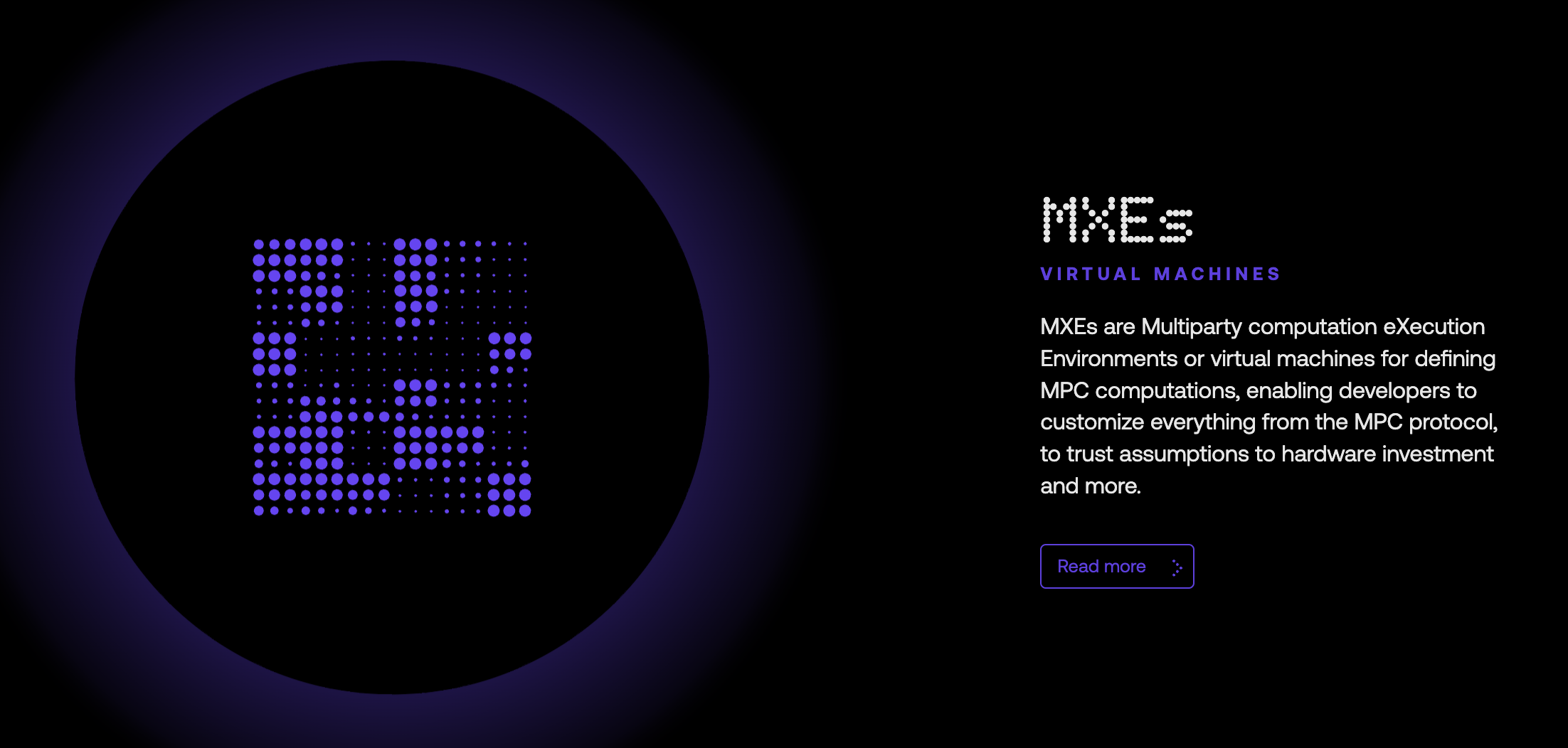
Oltre ai nodi Arx, Arcium introduce anche gli MXE, o Multiparty eXecution Environments. Questi MXE fungono da macchine virtuali per le computazioni multiparty sicure e consentono agli sviluppatori di configurare vari aspetti della computazione, tra cui gli schemi di crittografia, la selezione dei nodi e i parametri di esecuzione.
Inoltre, Arcium ha sviluppato una propria interfaccia di programmazione nativa, Arcis, progettata per scrivere applicazioni MPC sicure. Fornisce agli sviluppatori un'interfaccia familiare e intuitiva per la creazione di applicazioni che preservano la privacy e che possono elaborare dati crittografati all'interno di MXE isolati.
La rete Arcium offre configurazioni MPC personalizzabili, consentendo agli utenti di adattare i livelli di sicurezza, la selezione dei nodi e i protocolli di esecuzione alle loro esigenze specifiche. La flessibilità offerta da MPC rende Arcium adatto a un'ampia gamma di applicazioni, dall'addestramento di modelli di intelligenza artificiale all'analisi di dati medici.
Arcium sfrutta la tecnologia MPC in tutta la sua vasta gamma di prodotti per fornire una potente piattaforma di calcolo riservato che dà priorità alla privacy, alla sicurezza e alla collaborazione. Probabilmente una delle tecnologie DeCC più complete disponibili, MPC offre ad Arcium la flessibilità, la resilienza e le prestazioni necessarie per alimentare la sua rete in crescita.
Questo approccio posiziona Arcium come un attore chiave nello spazio del calcolo riservato decentralizzato, assicurando che il protocollo sia ben equipaggiato per facilitare le richieste di settori emergenti come DePIN, AI e soluzioni sanitarie basate su blockchain.
Per saperne di più su SolanaFloor
Il più grande protocollo di governance di Solana’si sta evolvendo
Realms rompe i legami con Solana Labs per formare un'entità separata
Video