“Programs on Solana are Fundamentally More Secure” - OtterSec Founder Weighs In Solana’s Low Exploit Rate
Data suggests EVM networks suffered over $792.6M in hacks throughout 2024, compared to $33.5M on Solana. What makes Solana safer?
- Published:
- Edited:
Despite the diligent work of auditors across the industry, blockchain hacks and exploits are still commonplace.
However, data indicates that certain networks and virtual machines are at far greater risk than others, with Solana enjoying a significantly reduced number of hacks when compared to its rivals.
Is Solana and the SVM inherently more secure than its competitors? Speaking with SolanaFloor, OtterSec founder Robert Chen dispelled some of the myths surrounding blockchain security.
Is the EVM a Happier Hunting Ground For Hackers?
According to DefiLlama data, EVM networks have suffered over $792M in hacks and exploits in 2024. Comparatively, Solana only endured a total $33.5M, with $14.8M of that figure due to the Rain crypto exchange exploit, which also targeted Bitcoin, Ethereum, and XRP wallets.
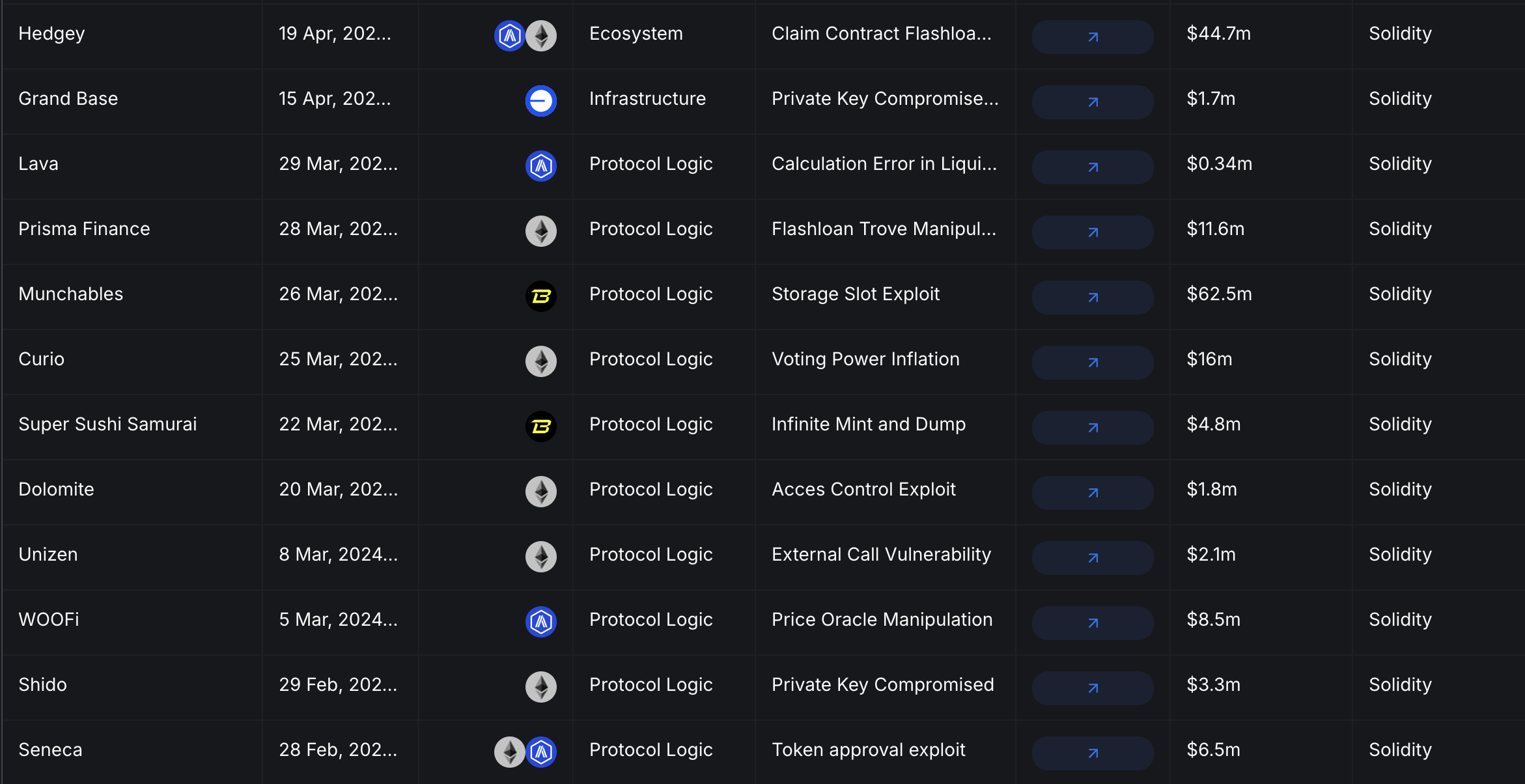
In the majority of recorded cases, hackers steal funds by finding vulnerabilities in protocol logic. Based on DefiLlama’s recordings, protocols on EVM networks fall victim to attacks on flawed logic more often than their Solana counterparts, despite the dramatic influx of capital and users to the Solana ecosystem in 2024.
Robert Chen, founder of OtterSec, one of the industry’s most reputable smart contract auditors argues that there are many factors contributing to this discrepancy. While admitting “it’s hard to say for sure”, Chen asserted “one theory is that programs on Solana are fundamentally more secure because of the programming model.”
“That's probably partially true in the sense that they had the benefit of hindsight when designing the VM, right? So for one, one big example is that there's no re-entrancy on Solana, which mitigates, a pretty large attack surface.”
Chen acknowledges that may not be “the full story”. The founder noted that Solana suffered several large-scale hacks and exploits of its own in 2022 and 2023. Additionally, Chen attested that some vulnerabilities “are fundamentally VM agnostic. For example, any sort of economic exploit is VM agnostic.”
While Solana has suffered a comparatively low number of hacks and exploits due to flawed protocol logic, this doesn’t take into account funds extracted through systematic onchain rugpulls. Solana’s meme economy features dozens of nefarious actors running looped scams, taking advantage of unwary traders.
Who’s Auditing the Auditors?
Over the years, Ottersec has earned itself a reputation as one of the industry’s most trustworthy auditors. However, hackers are becoming increasingly crafty, working relentlessly to discover new attack vectors.
According to Chen, the best way to stay ahead of new attack strategies is to apply new learnings retroactively and look deeper into the stack.
“Once you do a large number of protocols, you can take the learnings from one protocol and apply it to the other. If you notice something in one protocol, you can go back through and look at all the other protocols.”
“I think we also try to look very deep in the stack. For example, we do audits of the validator client, but then we also do audits of frameworks like Anchor. I think having that sort of expertise or at least that sort of exposure lets us look a little bit deeper than other people.”
Chen argues that the auditing business is about trust and bespoke relationships. Opinion, both public and private, is the main indicator gauging a firm’s ability to audit effectively.
“I think there's always an implicit check in the sense that if you mess up, not like once, but if you mess up a lot of times, word of mouth gets around, right?
When it comes to auditing firm reputation, there is currently no higher power or entity that ensures auditors are maintaining a certain standard. However, Chen argues that a higher body isn’t necessarily required.
“I think auditing is very bespoke in the sense that it's fundamentally a business about trust. There's no real central body that people like turning to, or, I mean, in my case, want to turn to, to get this trust about auditing standards. People have their preferred auditors, they know who they want to work with. Those sorts of bespoke relationships are hard to replace with a centralized party”
A successful audit isn’t a foolproof assurance that a protocol is completely vulnerability-free. However, as Chen aptly puts: “it's a game of probabilities”. Audited protocols are likely to have fewer bugs than unaudited protocols.
Crypto users should always be sure to complete thorough due diligence before interacting with onchain protocols and maintain rigorous security standards.
Read More on SolanaFloor
Crypto takes bolder steps into TradFi
How Does NYSE Arca’s Latest Filing Legitimize Solana ETFs?
Refresh Your Crypto Security Essentials